Database Security Monitoring & Management
for SQL Server, Azure SQL Database,
and Amazon RDS for SQL Server
SQL Secure
See who has access to what and
how permissions are granted
There are many different and complex ways to grant access to SQL Server. It is virtually impossible to manually analyze a security model across instances or determine rights of users on specific database objects. SQL Secure answers the important question, “Who can do what, where, and how on my SQL Server databases?” SQL Secure provides a comprehensive, automated solution for analyzing, monitoring and reporting on security access rights for SQL Servers including managed cloud databases.
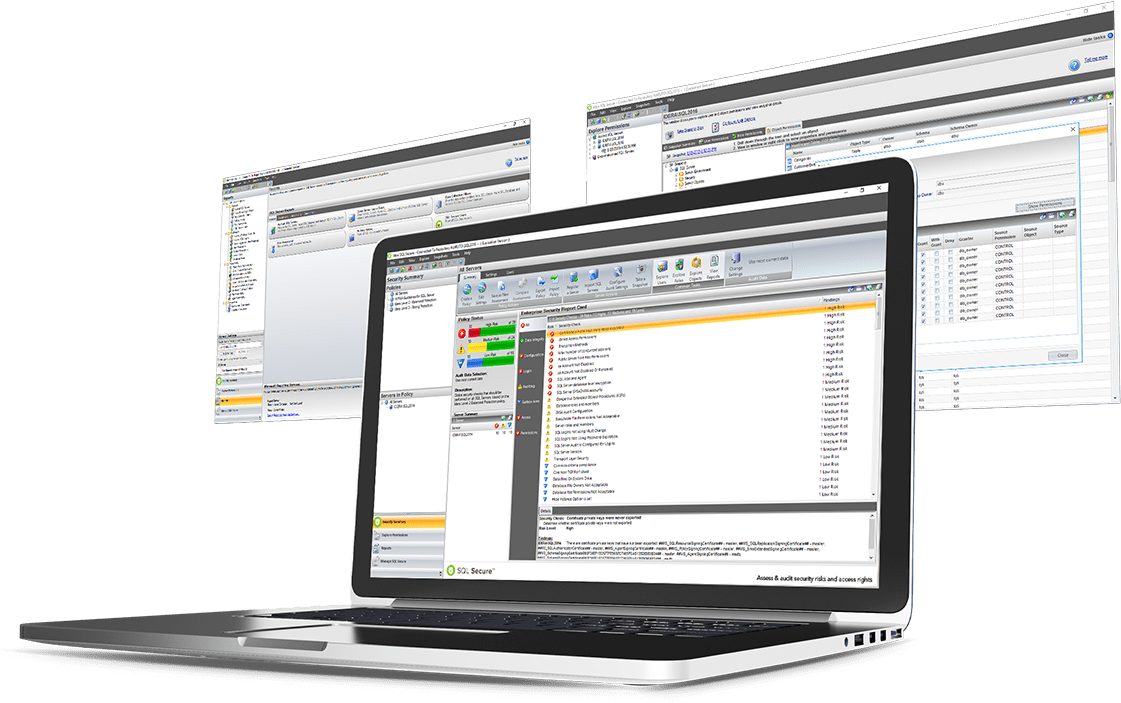
- Identify vulnerabilities and harden security policies.
- Rank security levels with the security report card.
- Analyze user permissions across database objects.
- Audit using templates for regulatory compliance.

-
Analyze effective rights
Analyze the effective rights of users to show how and where each right is granted. This makes it easy to pinpoint exactly what to change to close security holes.
-
View database roles permissions
View role members and sub-roles assigned and their effective permissions for SQL Server, Azure SQL Database, and Amazon RDS for SQL Server.
-
Analyze server object settings
Reduce data collection, transmission, and storage overhead with powerful filtering capabilities that enable you to collect only the data that is important for audit and compliance.
-
Detect weak passwords
Analyze password health of SQL Server logins and reports on passwords that are weak or blank which would cause a susceptible to intrusion situation.
-
Identify surface area and protocols
Identify services, ports, protocols, and application performance interfaces (APIs) that allow malicious users to attack SQL Server, Azure SQL Database, and Amazon RDS for SQL Server.
-
Analyze operating system security
Assess the setup of the operating system (OS) to identify issues that would compromise SQL Server security.
-
Analyze powerful users
Analyze the membership to powerful server roles and groups such as database, system, and security administrators to ensure this level of access is warranted.
-
Detect unresolved Windows accounts
View all logins on the target server, and any unresolved Windows accounts or groups.
-
View server security properties
Show all security-related properties for servers including the version and patch level, authentication mode, audit mode, proxy account, and cross database chaining.
-
Self-audit administration
Monitor all activity related to SQL Secure administration.
-
Use predefined policy templates
Audit for standards via distinct levels (basic, balanced, strong) that define realistic guidelines for protecting SQL Server from common intrusion attacks.
-
Analyze reporting services
Show details of services such as log-on and configuration.
-
Generate security scorecard
List potential security concerns such as cross-database chaining and drill down to view the full details of the diagrammed relationships.
-
View history and baselines
The SQL Secure repository keeps a complete history of SQL Server security settings to designate a baseline to detect changes.
-
Run powerful reporting
Access built-in standard reports and create custom reports to provide detailed information for security auditing and compliance.
-
Assess risk
Security audit rules provide visibility for database access checks, configuration checks, and permission checks.
-
Check security
Increase security audit coverage via additional checks for data protection, encryption, and firewall rules.
-
Report across servers
Show security state from a global view (for example, all instances with guest accounts enabled).
-
Manage from central console
Manage the creation of collection rules and policies, view risks and assessments, monitor collection history, and analyze user access rights via a single point of control.
-
Configure data collection
Define what security information to gather and when. Gather from physical, virtual, and cloud hosts, operating systems, file systems, Registry, and Active Directory.
-
Store data in central repository
SQL Secure stores all security data collected in a central repository for easy reporting and forensic analysis.
-
Use flexible views
Use the flexible grid view to audit and analyze user permissions. Sort, group, or export all SQL Server logins in the enterprise.
-
Automate server registration
Support for large SQL Server environments with significant gains in time to value via the comma-separated values (CSV) file import process.
-
Tag server groups
Assign servers to groups, then view and manage security policies according to group designations.
-
Install on cloud virtual machines
Unify control by running SQL Secure on cloud virtual machines with Windows—such as Azure Virtual Machine (VM) and Amazon Elastic Compute Cloud (EC2).
-
Monitor SQL Server on cloud virtual machines
Monitor SQL Server instances running on cloud virtual machines—such as Azure VM and Amazon EC2.
-
Monitor hybrid environments with a single tool
Save time by using the same performance-monitoring tool for SQL Server databases on physical and virtual machines on-premises; on virtual machines in the private, public, and government cloud; and as managed databases in the public and government cloud.
-
Access mapped cloud drives
Map cloud storage as network drives or removable drives on Windows. For example, map storage to Amazon Simple Storage Service (S3) and Azure Blob Storage.
-
Monitor managed SQL Server cloud databases
Extend cloud capabilities with monitoring the managed cloud databases Azure SQL Database and Amazon RDS for SQL Server.
Let’s get started.
Start your 14-day trial, no credit card required (but all fields are).
Commercial licenses are not supported with this trial download. To update to the latest version, please access IDERA’s customer support portal.
Ready to see how SQL Secure can help you monitor and manage SQL Server security on-premises and in the cloud?

SQL Secure
Datasheet
Everything you need to know,
all in one downloadable PDF.
Are You Ready for GDPR?
See how to comply with GDPR
and improve database auditing
and management

Why Use
SQL Secure?
Learn about the key features of SQL Secure to help you improve your SQL SQL Server security

Value of
SQL Secure
Learn about the benefits of SQL Secure for you and your organization
Database Security Risks You Haven’t Considered, But Need To
Kevin Beaver shows how you can be more proactive with database security
Nuts and Bolts of
Permissions and Security
Pinal Dave presents the basic fundamental blocks of SQL Server permissions and security.
